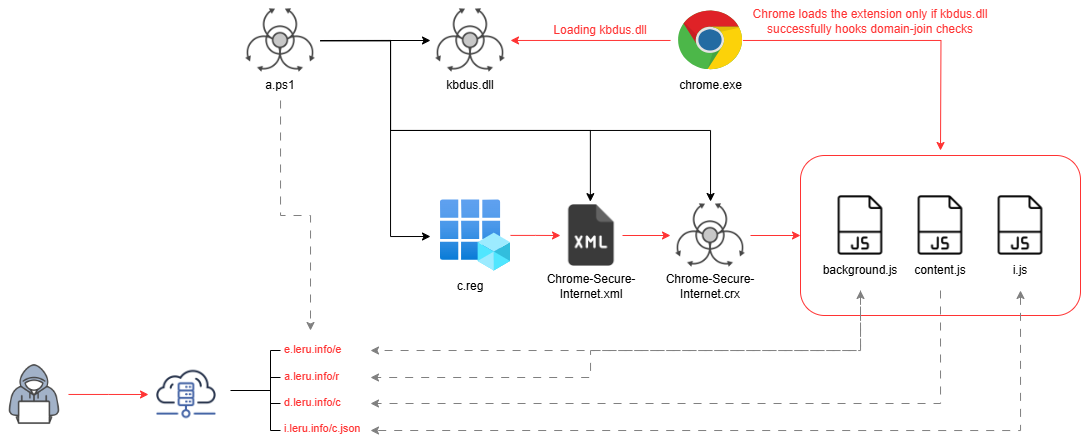
User consent bypass by browser extension : an adware case study
This article provides a comprehensive analysis of a little-documented threat, which is a Chrome extension distributed by a powershell script. Its objective is not to compromise the workstation, but to monetize user traffic...
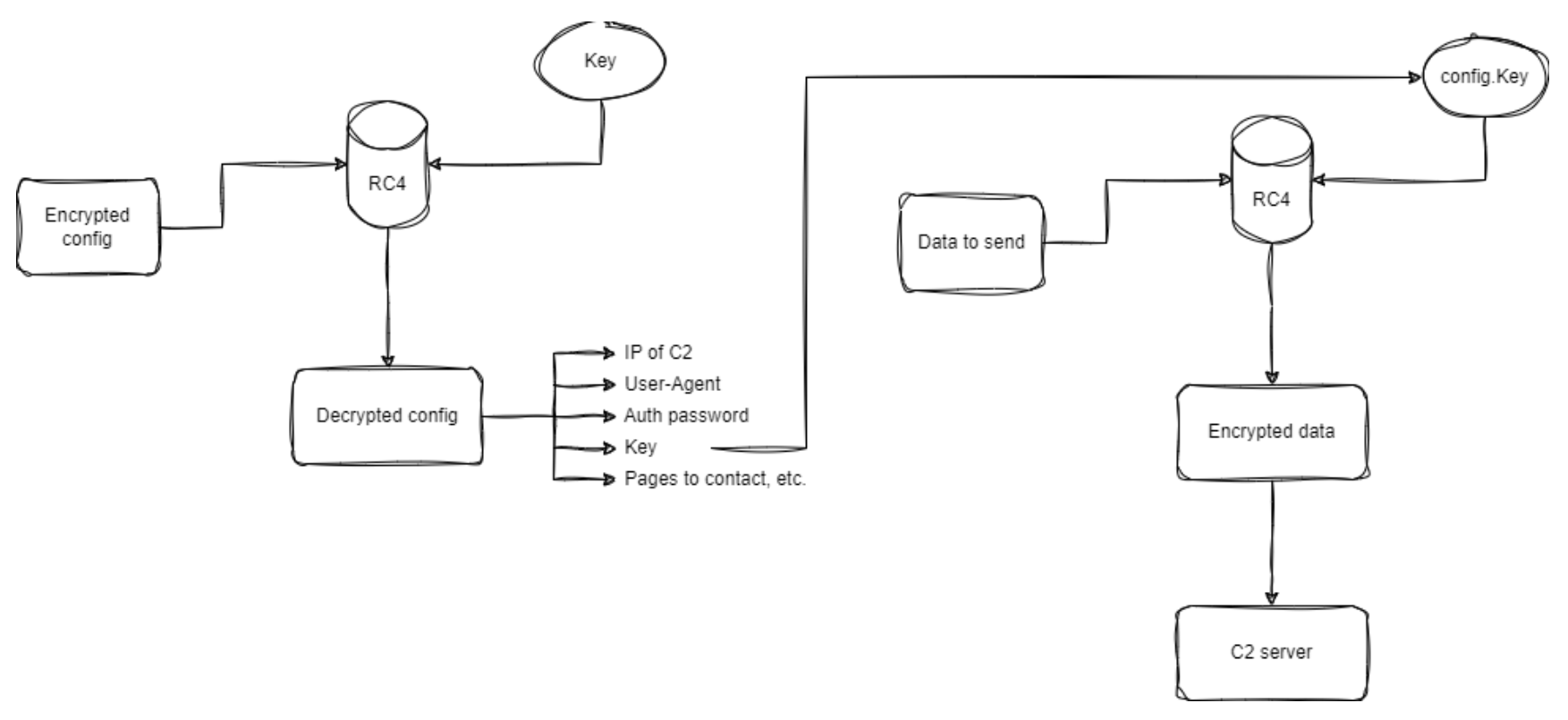
#Malware # #C2 # #Reverse # #BrowserIncident Response: Analysis of recent version of BRC4
During our latest incident response case we have discovered a recent sample of Brute Ratel C4 packed with Themida. BRC4 is a powerful Command and Control (C2) tool which allows to control targeted workstations through an executable agent...
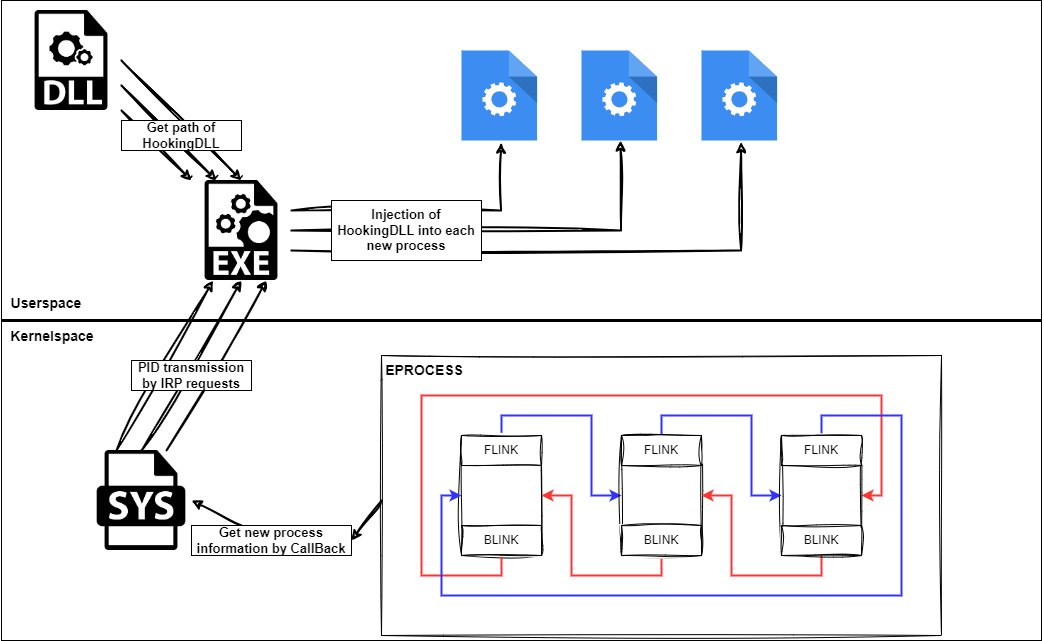
#Malware #Detection #Reverse #C2WinAPI Hooking
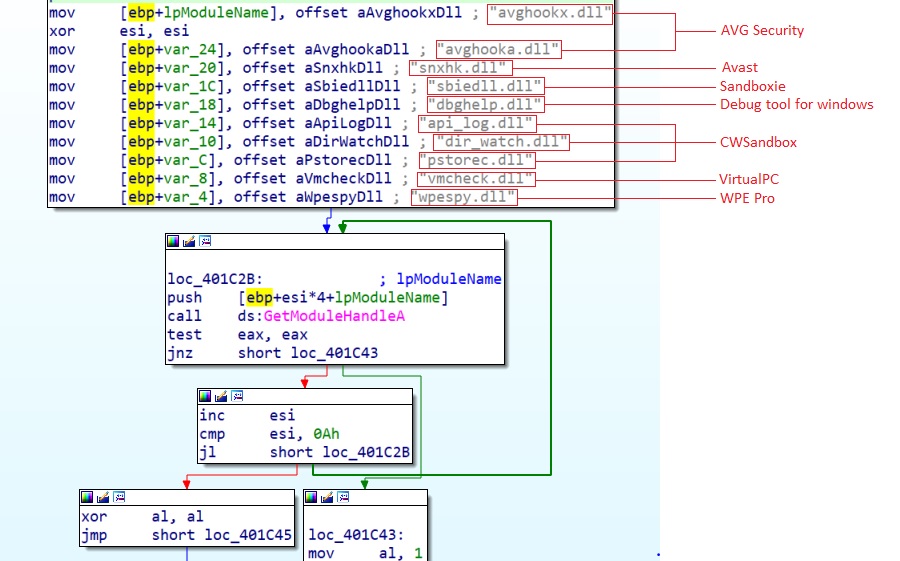
This article focuses on the study of injection for hooking Windows API functions. We'll explore what hooking is, how it works and how it's implemented...
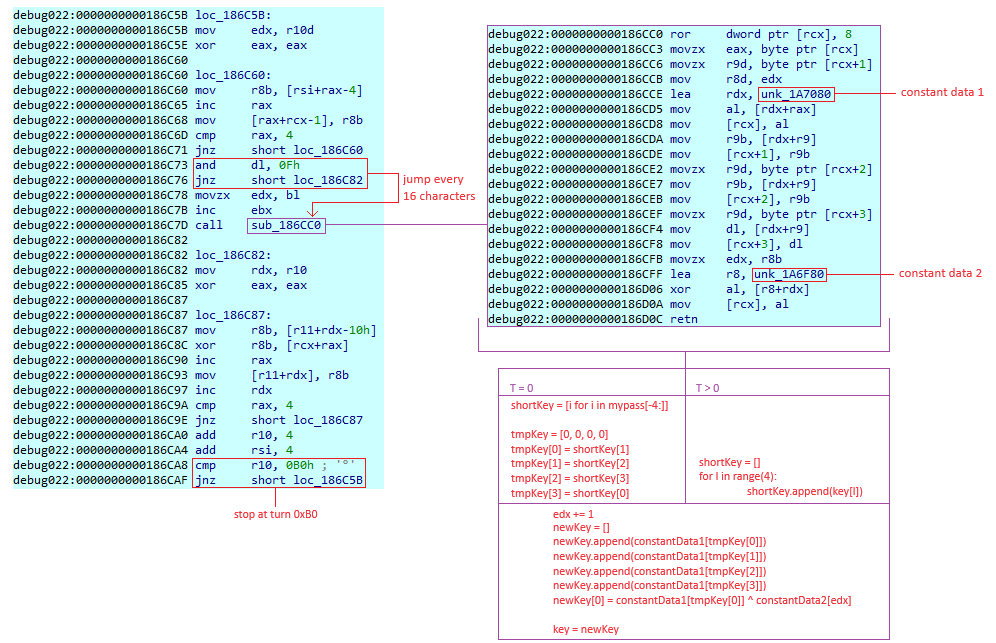
#Malware #Hooking #Detection #ProgrammingBrute Ratel BRC4
This article will not be a detailed malware analysis report on the features of Brute Ratel (BRC4), but rather a study focusing on several samples of the same version...
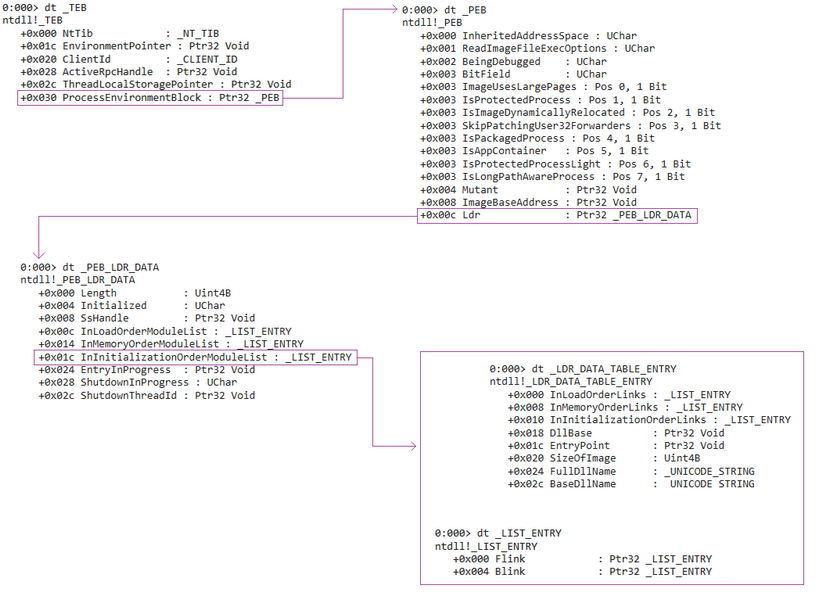
#Reverse #Malware #C2PEB Parsing & API Hashing
In this article, we'll take a look at how the API hashing technique works and how to defeat it...
#Reverse #Technique #Obfuscation